In the vast digital landscape where websites are the heart and soul of businesses big and small, protecting your online presence has become more crucial than ever before. While the Internet offers limitless opportunities, it also attracts nefarious forces seeking to exploit vulnerabilities for their own gain. It’s like a battle between David and Goliath, but fear not! In this article, we will arm you with knowledge and guide you through the treacherous pathways of website security, with a special focus on two formidable enemies: brute force attacks and SQL injections. By understanding their nature and implementing robust defenses, you can fortify the bulwarks of your website against these relentless assailants. So grab your virtual armor, as we embark on a journey to shield your online sanctuary from the darkest corners of the web!
Preventing Brute Force Attacks: Strengthening Your Website’s Security

In today’s digital landscape, it is crucial to fortify your website’s security against malicious attacks. Brute force attacks and SQL injections are two common threats that can compromise the integrity and functionality of your website. Fortunately, by implementing effective preventive measures, you can significantly reduce the risk of falling victim to these cyber attacks.
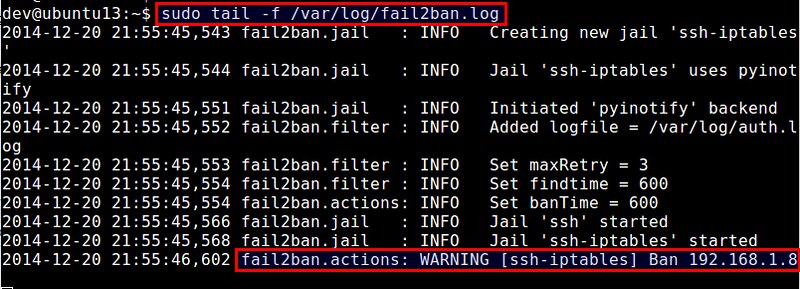
When it comes to preventing brute force attacks, there are several key steps you can take to strengthen your website’s defense. Firstly, consider implementing a strong and complex password policy for all user accounts. Encourage users to create passwords that are at least 10 characters long and include a mix of upper and lowercase letters, numbers, and special symbols. Additionally, enforcing password expiration and regular password updates can further enhance security. Secondly, implementing account lockouts after a certain number of failed login attempts can frustrate potential attackers by limiting their brute force capabilities. By configuring your website to automatically lock an account for a designated period of time, you can discourage attackers from persistently trying to crack login credentials. Lastly, consider implementing a two-factor authentication system. This additional layer of security adds an extra step for users to verify their identity, typically through a code sent to their mobile device or email. This significantly reduces the risk of brute force attacks as even if an attacker manages to obtain login credentials, they still require the second authentication factor to gain access.
Understanding SQL Injections: Identifying Vulnerabilities
In today’s digital age, website security is paramount. One of the most common and dangerous threats that website owners face is the risk of brute force attacks and SQL injections. These malicious attacks can lead to unauthorized access to sensitive data, website defacement, and even complete data loss. To prevent these attacks from wreaking havoc on your website, it is crucial to understand their nature and how to identify vulnerabilities.
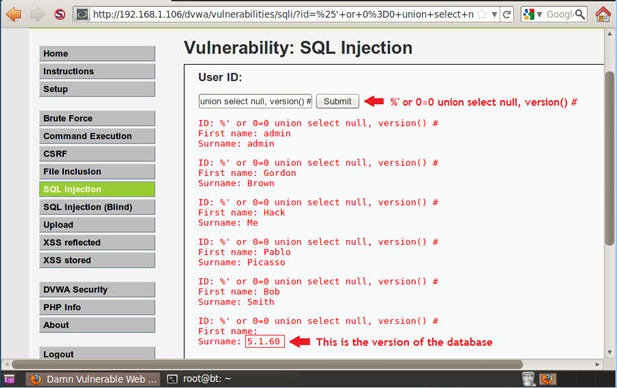
A SQL injection occurs when an attacker manipulates a website’s database query to execute arbitrary commands. This vulnerability arises when user-supplied data is not properly sanitized or validated before being used in a SQL query. By exploiting this weakness, an attacker can bypass authentication, extract sensitive information, modify database content, or even destroy the entire database. Identifying vulnerabilities is the first step towards securing your website against SQL injections. Here are some key indicators:
- Unsanitized user inputs that are directly used in database queries
- Error messages that reveal sensitive information about the database structure or query execution
- Excessive or unusual database error logs
By being aware of these signs, you can take proactive measures to mitigate the risk of SQL injection attacks. Regularly update your website’s software and plugins, as outdated versions may contain vulnerabilities that can be exploited. Use parameterized queries or prepared statements to ensure the separation of data and code, making it impossible for attackers to inject malicious code. Finally, employing a web application firewall (WAF) can provide an additional layer of protection by filtering out suspicious requests and blocking potential attacks. With a thorough understanding of SQL injections and the vulnerabilities they exploit, you can fortify your website’s defenses and keep your valuable data safe.
Implementing Strong Password Policies: Safeguarding Access

Having a strong password policy in place is crucial to safeguarding access to your website and protecting it from potential threats such as brute force attacks and SQL injections. In this post, we will discuss some practical steps and best practices that you can implement to strengthen your website’s defenses and keep your valuable data secure.
1. Enforce complex passwords:
- Set a minimum password length of at least 8 characters.
- Encourage the use of a combination of uppercase and lowercase letters, numbers, and special characters.
- Regularly prompt users to update their passwords to enhance security.
2. Implement multi-factor authentication:
- Add an extra layer of security by requiring users to provide additional authentication factors, such as a one-time password (OTP) sent via SMS or email.
- Consider using biometric authentication methods, like fingerprint or facial recognition, for added protection.
Securing User Input: Best Practices for Validating SQL Queries

In today’s digital landscape, protecting your website from malicious attacks is of utmost importance. Brute force attacks and SQL injections pose significant threats to the security of your user data and the overall integrity of your website. To safeguard your website and ensure the utmost security, it is essential to implement best practices for validating SQL queries. Here, we will delve into some tried and tested methods to secure user input effectively.
1. Parameterized queries: One of the most effective ways to prevent SQL injections is by using parameterized queries. These queries separate the SQL code from the user input, significantly reducing the risk of injection attacks. With parameterized queries, the user input is treated as data and not as executable code, thus preventing attackers from manipulating the query structure.
2. Input validation: Another critical aspect of securing user input is thorough input validation. Ensure that your website performs rigorous data validation by checking the input against predetermined rules or patterns. Implementing client-side validation using JavaScript and server-side validation using a back-end programming language adds an extra layer of security. Regular expressions can be handy in detecting and blocking any suspicious or potentially harmful input.
3. Escaping characters: It is essential to escape characters before including them in SQL queries to prevent potential SQL injections. Certain characters, such as single quotes or backslashes, can alter the structure of a query and allow attackers to execute unauthorized commands. By escaping these characters using appropriate methods provided by your programming language or framework, you can neutralize the risk of injection attacks.
4. Limiting privileges: Restricting the privileges of database accounts used by your website is an essential security measure. By granting minimal privileges required for the website’s functionality, you minimize the potential damage an attacker can inflict in case of a successful injection attack. Implementing the principle of least privilege ensures that even if an attacker gains access to the database, they won’t be able to alter critical data or execute harmful commands.
By implementing these best practices for validating SQL queries, you can significantly enhance the security of your website and protect it from brute force attacks and SQL injections. Prioritizing the safeguarding of user data should be at the forefront of your website development strategy. Stay one step ahead of malicious attackers and ensure a safe browsing experience for your website visitors.
Effective Use of Prepared Statements and Stored Procedures

In the quest to safeguard your website from potential threats, it is crucial to understand the importance of utilizing prepared statements and stored procedures effectively. These powerful tools not only help prevent brute force attacks but also play a pivotal role in mitigating the risk of SQL injections.
Prepared statements serve as a shield against SQL injections by separating the SQL logic from the data inputs. By utilizing parameterized queries, potential hackers are unable to inject malicious code into your database. Additionally, prepared statements offer other benefits such as improved performance and code reusability. When implementing prepared statements, remember to bind variables to the SQL statement, ensuring that user inputs are treated as data and not executable code. This drastically reduces the chances of successful SQL injections.
Stored procedures are another essential aspect of securing your website from potential threats. By creating and utilizing stored procedures, you can minimize the exposure of your database structure to external attacks. Storing reusable SQL code within the database itself allows for easier maintenance, reduced code duplication, and consistent execution of SQL statements. Furthermore, stored procedures help enforce access control, as they can be granted or revoked based on user privileges. By incorporating stored procedures into your website’s architecture, you add an additional layer of protection against brute force attacks and unauthorized access.
In the ever-evolving landscape of web security, taking proactive measures to protect your website is of utmost importance. And with the , you can significantly reduce the risk of brute force attacks and SQL injections, ensuring the integrity and security of your website and its valuable data.
Utilizing Web Application Firewalls: A Layer of Protection

Web application firewalls (WAFs) are becoming an indispensable line of defense against the ever-evolving cyber threats that target websites. By implementing a WAF, you can shield your website from malicious attacks such as brute force attacks and SQL injections. Brute force attacks can be devastating, with hackers using automated methods to guess login credentials and gain unauthorized access to your website. On the other hand, SQL injections exploit vulnerabilities in web applications, allowing attackers to manipulate databases and access sensitive information.
Fortunately, a WAF acts as an additional layer of protection, mitigating these threats and preserving the integrity of your website. It works by examining incoming traffic and analyzing it against a set of predefined security rules. If any suspicious activity is detected, the WAF takes appropriate action, such as blocking or alerting the network administrator. With its real-time monitoring and advanced filtering capabilities, a WAF ensures that all incoming requests are thoroughly inspected, preventing illegitimate access attempts and safeguarding your data.
When it comes to securing your website, prioritizing the implementation of a WAF is essential in today’s cyber landscape. Here are some key benefits of utilizing a WAF:
– Continuous threat detection and prevention: With a WAF in place, you can proactively identify and block potential threats before they can cause harm. The WAF’s robust set of security rules and algorithms constantly monitors your website, keeping it safe from both known and emerging attack vectors.
– Protection against zero-day vulnerabilities: Zero-day vulnerabilities refer to newly discovered software flaws that hackers exploit before developers can provide a patch or fix. A WAF can provide a crucial defense against such vulnerabilities by applying heuristic analysis techniques to identify suspicious patterns and behaviors, thereby offering immediate protection to your website.
By integrating a WAF into your website’s security framework, you can enhance its defense against brute force attacks and SQL injections, providing peace of mind to both you and your website visitors.
Monitoring and Logging: Detecting and Responding to Attacks

With the increasing complexity of cyber threats, it is crucial for website owners to prioritize their security measures. Monitoring and logging play a significant role in detecting and responding to attacks effectively. By implementing these practices, you can safeguard your website from brute force attacks and SQL injections.
Monitoring is the process of actively observing and tracking the activities on your website, allowing you to identify any suspicious behavior or unauthorized access attempts promptly. By setting up real-time monitoring tools, such as intrusion detection systems (IDS), you can receive immediate notifications when an attack is detected. Additionally, logging provides a valuable resource for analyzing and investigating security incidents. By generating detailed logs of all web server activities, you can gain insights into the potential vulnerabilities or attack patterns that perpetrators may exploit.
To protect your website from brute force attacks, it is crucial to implement measures that limit repeated login attempts. Consider implementing CAPTCHA challenges to differentiate between human users and malicious bots. Additionally, enabling account lockouts after a certain number of failed login attempts and implementing two-factor authentication can significantly enhance your website’s security.
In the case of SQL injections, it is important to regularly update and patch your website’s software, as outdated versions often contain known vulnerabilities. Utilize parameterized queries or prepared statements to ensure that user inputs are properly validated and sanitized. Implementing a web application firewall (WAF) can also provide an extra layer of protection by analyzing and filtering incoming web traffic for any suspicious or malicious SQL injection attempts.
By being proactive in monitoring and logging, and implementing robust protection measures against brute force attacks and SQL injections, you can mitigate potential security risks and protect the integrity of your website. Stay one step ahead of attackers by regularly reviewing your security practices and staying up to date with the latest security best practices in the industry.
Regular Security Audits: Ensuring Ongoing Protection

Regular security audits are an essential component of maintaining a robust and secure website. By conducting regular audits, you can ensure ongoing protection against potential threats such as brute force attacks and SQL injections. These security measures are crucial for safeguarding your website and keeping your sensitive data out of the wrong hands.
One of the most effective ways to protect your website from brute force attacks is by implementing strong and unique passwords for all user accounts. Encourage users to create passwords that are a combination of uppercase and lowercase letters, numbers, and special characters. Additionally, consider implementing multi-factor authentication (MFA) for an added layer of security. MFA requires users to provide two or more methods of identification, usually a password and a unique code sent to their mobile device, further reducing the risk of unauthorized access.
Another common website vulnerability is SQL injections. To protect your website from such attacks, it is important to perform regular code reviews and ensure that all inputs are properly validated and sanitized. Implementing parameterized queries and stored procedures can help prevent SQL injection attacks by ensuring that user inputs are treated as data and not executable code. Regularly updating your website’s software and plugins is also essential to eliminate known vulnerabilities, as developers often release security patches to address vulnerabilities as they are discovered.
In conclusion, regular security audits are pivotal in guaranteeing ongoing protection for your website. By implementing measures such as strong passwords, multi-factor authentication, code reviews, and regular updates, you can fortify your website against brute force attacks and SQL injections. Always stay vigilant and proactively address potential security risks to ensure the safety of your data and maintain the trust of your users.
Insights and Conclusions
In a digital world brimming with ambitious hackers and persistent attackers, safeguarding your website from brute force attacks and SQL injections is no longer an option—it’s a necessity. By equipping yourself with the knowledge and tools to fortify your virtual fortress, you can ward off these relentless threats and maintain the integrity of your online presence.
Remember, vigilance is key. Continuously monitoring your website’s security measures, updating software, and adhering to best practices will keep potential vulnerabilities at bay. By implementing strong passwords, multi-factor authentication, and limited login attempts, you erect an impenetrable barrier that even the most audacious assailants will struggle to breach.
But the battle doesn’t end there. Protecting against SQL injections requires a deeper understanding of your website’s architecture and how attackers exploit vulnerabilities. Stay ahead of the game by utilizing robust input validation techniques, prepared statements, and stored procedures. By fortifying your codebase, you can prevent malicious entities from gaining unauthorized access to your precious data.
While the threat landscape may evolve and new vulnerabilities may emerge, armed with the knowledge and tools gained from this article, you are well-equipped to resist the relentless onslaught of brute force attacks and SQL injections. Remember, every line of code carries the weight of your online security, and it’s your responsibility to ensure its impenetrability.
So, fellow guardians of the digital realm, let us never waver in our quest to protect what’s rightfully ours. By dismissing complacency and embracing a proactive defense, we can persevere against those who seek to exploit our online domain. Together, we can uphold the sanctity of our websites and preserve the trust of our users.